Cloudflare Blocks Record-Breaking DDoS Attack Reaching 3.8 Tbps
Cloudflare has revealed that it successfully blocked a massive distributed denial-of-service (DDoS) attack that peaked at 3.8 terabits per second (Tbps) and lasted for 65 seconds.
The company reported that it defended against more than 100 large-scale Layer 3/4 DDoS attacks throughout the past month. Many of these attacks exceeded 2 billion packets per second (Bpps) and 3 Tbps. These attacks, ongoing since early September 2024, targeted several customers in the financial, internet, and telecom sectors. No specific group has been blamed for the attacks.
The previous record for the largest DDoS attack was 3.47 Tbps in November 2021, which targeted a Microsoft Azure customer in Asia.
The recent attacks used the User Datagram Protocol (UDP) on a fixed port, with the packet floods coming from countries like Vietnam, Russia, Brazil, Spain, and the U.S. The attackers used compromised devices such as MikroTik routers, DVRs, and web servers.
Cloudflare suspects these high-speed attacks are powered by a large botnet of infected ASUS home routers, which were compromised by a critical flaw (CVE-2024-3080) with a CVSS score of 9.8. According to Censys, over 157,000 ASUS routers were potentially affected by this flaw as of June 2024, with many located in the U.S., Hong Kong, and China.
Attack Goals and Defense
Cloudflare explained that the goal of these DDoS attacks is to overwhelm the target’s network bandwidth and CPU resources, making it difficult for legitimate users to access the service.
“To protect against high packet rate attacks, it’s crucial to inspect and discard bad packets quickly, using minimal CPU resources, so that the good packets can be processed,” the company said.
They also noted that many cloud services and on-premise equipment don’t have enough capacity to defend against attacks of this scale. High bandwidth usage can clog internet connections, while high packet rates can crash in-line devices.
DDoS Attacks on the Rise
Banking, financial services, and public utilities have been increasingly targeted by DDoS attacks, with a 55% increase over the last four years, according to NETSCOUT. In the first half of 2024 alone, there has been a 30% rise in volumetric attacks.
The rise in DDoS attacks is largely driven by hacktivist groups targeting global organizations. These attacks are also becoming harder to detect, as hackers use DNS-over-HTTPS (DoH) to hide command-and-control (C2) traffic.
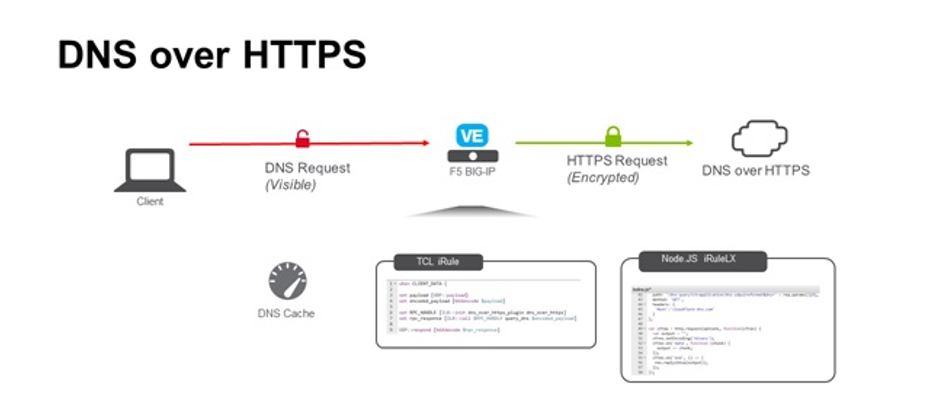
NETSCOUT added that attackers are using distributed botnet C2 infrastructures, making defense harder. This is because both inbound DDoS traffic and outbound traffic from infected bots need to be blocked.
New Threats from CUPS Vulnerabilities
Akamai recently warned that vulnerabilities in the Common UNIX Printing System (CUPS) in Linux could be exploited for DDoS attacks with a 600x amplification factor. More than 58,000 devices connected to the public internet are potentially at risk.
Researchers explained that attackers can send a specially crafted packet that tricks the CUPS server into sending larger requests to the target. This not only affects the target but also the CUPS server, consuming its bandwidth and CPU resources.
Censys estimated that around 7,171 hosts with CUPS services exposed over TCP are vulnerable to the CVE-2024-47176 flaw, but the actual number may be higher since more CUPS services are accessible over UDP than TCP.
Recommendations for Organizations
To protect against these threats, organizations are advised to remove CUPS if it’s not necessary. If CUPS services are needed, it’s important to firewall the service ports (UDP/631) to prevent access from the broader internet.







