Introduction
OverlayFS is a powerful filesystem technology that allows you to layer multiple filesystems on top of one another, merging them into a single unified view. In this CTF, you’ll explore the functionalities of OverlayFS, learning how it facilitates efficient storage management and simplifies the organization of data.
Setup Environment
Join OverlayFS CTF room on TryHackMe by clicking HERE.
Through TryHackMe: The process of setting up environment and connecting to the machine is a part of our CTF. So simply follow the provided steps below to finish this short yet engaging CTF.
Note: The vulnerability targeted in this CTF has been patched already, and the focus is on understanding the concept behind that vulnerability and exploring potential actions within a system once it’s exploited.
OverlayFS CTF – Tasks
Task 1: What is OverlayFS?
Question: I have a very rough overview of what OverlayFS is…
Answer: No Answer Needed
CVE-2021-3493 – OverlayFS Exploit
Credentials for SSH are written below…
Username: overlay
Password: tryhackme123
OverlayFS CTF Solving
Below are solutions to the questions asked in your OverlayFS Capture The Flag (CTF) challenge.
Question 1: Deploy the machine with the Start Machine button in this task and wait up to 2 minutes for the VM to boot – No Answer Needed.
Note: Please utilize the Attackbox machine provided by TryHackMe for future exploits. The terminal accessible by clicking “Start Machine” doesn’t support copying and pasting content from outside sources, so using Attackbox will allow for seamless execution of exploits.
Question 2: SSH into the machine with the credentials provided in the task text – No Answer Needed.
Command: ssh overlay@MACHINE-IP
Question 3: Grab the source code for the exploit from SSD-Disclosure here and save it as exploit.c on the target machine.
Solution: Type nano exploit.c on your attackbox terminal and save the code inside it you got by clicking the above link
Question 4: Compile the exploit with gcc. If you’re finding this difficult, a command is given in the hints.
Command: gcc -o exploit exploit.c.
Question 5: Run your compiled exploit, and get root! What’s the flag in /root/?
Solution: To run the exploit, type ./exploit in your terminal and you will get a bash shell. Now change your directory to the root folder by cd /root/ command. You can see a file called flag.txt by ls command inside root directory. Copy the content inside that file and paste it in the last answer slot of you CTF.
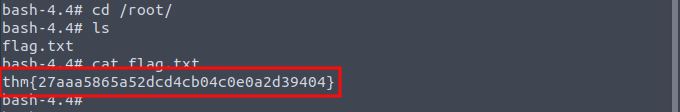
That your OverlayFS CTF machine, it’s a very short machine just an introduction of a critical vulnerability that has been patched very long time ago. So make sure to try other CTF machines as it makes your skills sharp and up to date.
Checkout our Mr. Robot CTF Walkthrough by clicking here.






